Unlock unparalleled defense against cyber threats with our External Attack Surface Management. Strengthen your security posture, proactively identify vulnerabilities, and keep your organization resilient in an ever-evolving threat landscape.
Stay one step ahead of potential breaches and safeguard your digital assets. See your organization the way bad actors can.
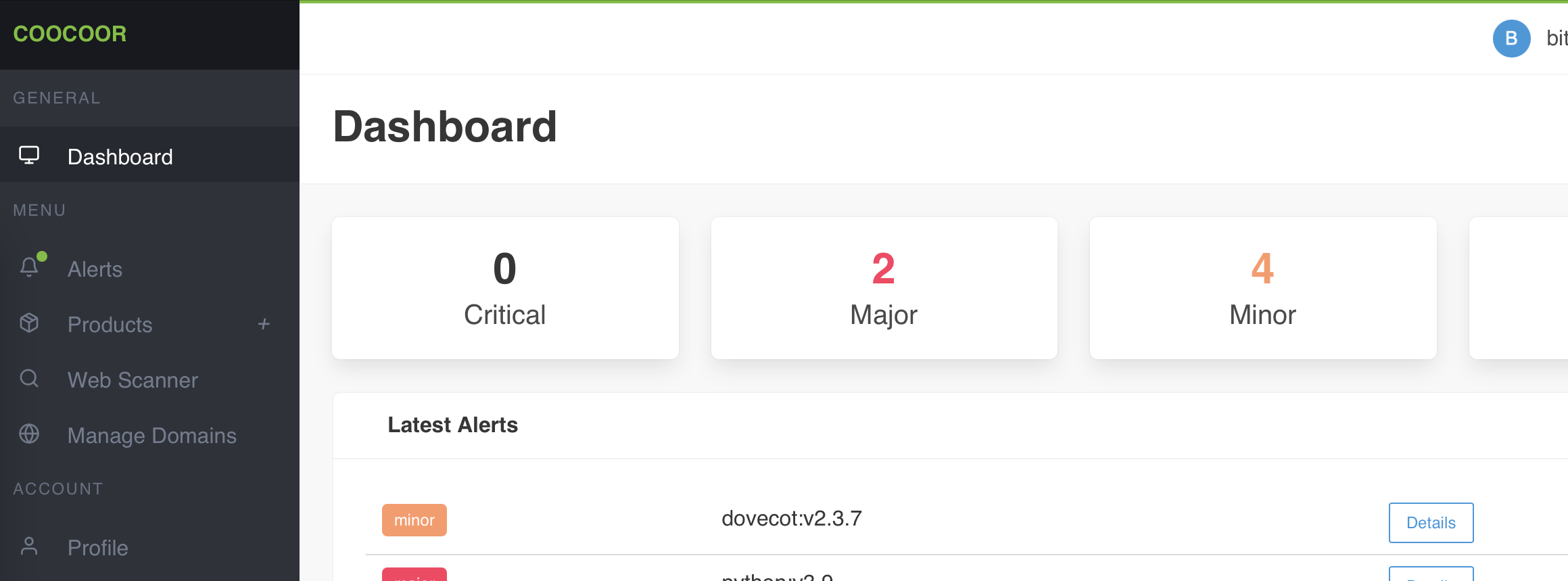
Constantly scan and monitor your organization's external attack surface, including websites, domains, IP addresses and cloud assets.
Identification of potential vulnerabilities, misconfigurations, weak points, or exposed assets that could be targeted by attackers.
Automatic discovery and inventory of your digital assets, providing you with a comprehensive view of your attack surface and ensuring no critical assets are overlooked.
Instant notifications and alerts for newly discovered vulnerabilities or changes to your attack surface, ensuring you can respond quickly and effectively. We provide seamless integration with Jira, Slack and Mattermost.
Enhanced security: Proactively identifies and mitigates vulnerabilities before they can be exploited by attackers.
Comprehensive visibility: Provides a clear view of an organization's attack surface, enabling better decision-making regarding security measures.
Compliance adherence: Helps meet industry standards and regulatory requirements through continuous monitoring and risk assessment.
Improved incident response: Enables faster detection and response to potential threats, reducing the impact of security incidents.
Protection of digital assets: Safeguards critical systems, websites, and other digital assets from unauthorized access and data breaches.
Learn More
External Attack Surface Management platform with the power of simplicity.
We gather intelligence by scanning and discovering all the digital assets associated with your organization, such as websites, domains, IP addresses, cloud assets, software components and online presence. We continuously monitors these assets to keep track of any changes or additions that may occur over time.
Once the assets are discovered and monitored, our application actively searches for vulnerabilities and potential security weaknesses. It examines various factors such as outdated software versions, misconfigurations, exposed services, or weak security protocols that could be exploited by attackers. By leveraging advanced techniques and intelligence, it identifies potential entry points that pose a risk to your organization's security.
After identifying vulnerabilities, our application assesses the risks associated with each vulnerability. It considers factors such as severity, impact, and exploitability to prioritize the risks effectively. The application then provides you with actionable insights and recommendations on how to remediate the identified vulnerabilities. These recommendations may include specific steps, best practices, or configuration changes to strengthen your security posture and mitigate the risks.
Switch plans or cancel any time. If you are a startup, we offer our Basic plan free for one year to help you establish a strong security foundation without financial burden during your initial growth phase. Please note that the free Startup Plan is applicable only for eligible startups and covers the first year of usage.
Continuous monitoring for 10 digital assets.
Vulnerability detection.
Real-time alerts.
Basic risk assessment.
Remediation guidance.
Suitable for small business or organizations looking for essential attack surface protection on budget.
Continuous monitoring of up to 50 digital assets.
Vulnerability detection.
Real-time alerts with priority support.
Comprehensive risk assessment.
Actionable insights.
Compliance monitoring.
Integration with threat intelligence feeds.
Ideal for mid-sized organizations that require a robust external attack surface management solution with additional features and enhanced support.
Unlimited digital assets monitoring.
Advanced threat detection.
Customizable reports and dashboards.
Advance compliance monitoring.
Dedicated customer support.
Perfect for organizations with complex IT infrastructures and high-security demands, ensuring maximum protection and scalability.
Below you'll find the answers to the questions we get asked the most.
Software/Hardware Components
Vulnerability Database
Digital Assets Monitored
Notifications Sent
Stay informed with product updates and security tips delivered to your inbox; no spam.